You can access the tool by clicking here
I've been working on something I think you'll find useful – a tool I'm calling Local Encryption, which helps you keep files truly private via your web browser. It’s built around the principle that you should have full control over your own data.
With Local Encryption, everything happens right on your device, in your web browser. When you encrypt or decrypt a file, it’s not uploaded anywhere. No servers, no third-party handling. Just you and your files.
I would also love to point out that this application is being hosted on Arweave, which means this application will be hosted permanently. The website itself cannot be directly altered or removed.
So, What is Local Encryption?
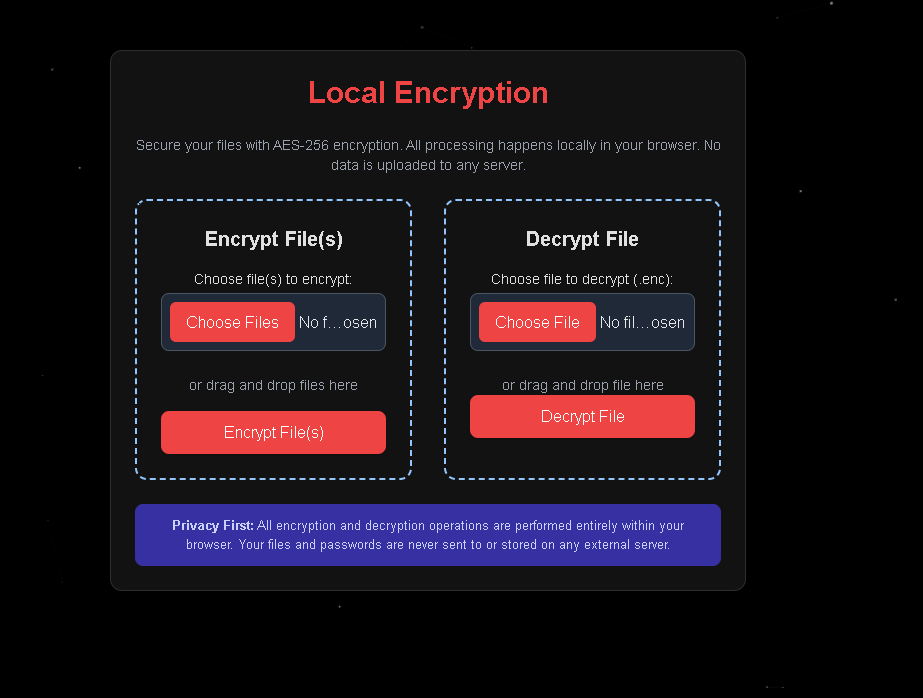
Simply put, it’s a webpage that lets you password-protect your files. You can lock them up, and then unlock them when you need them again. The core design is about providing strong security without unnecessary complexity, and ensuring privacy because the process never leaves your machine.
Getting Started: Using the Tool
The process for encrypting and decrypting is meant to be clear.
Encrypting Your File(s):
- Choose Your File(s): Look for the "Encrypt File(s)" area. You can click the "Choose file(s) to encrypt" button. Or, if you prefer, you can drag files from your computer and drop them right onto this spot. It handles single or multiple files.
- Set the Password: A box will pop up. Here, you type in the password you want to use for encrypting. You’ll type it a second time, just to confirm you’ve got it right. Then hit "Submit." (I’ve also added a password generator, which I'll get to).
- Encryption in Progress: The tool will then work on encrypting your file(s). You'll see a progress bar and some messages in a log area on screen, showing you what it's doing.
- Download Your Encrypted File: Once it's finished, you'll be able to download the encrypted result. This will be a single file, usually ending in
.enc(it's actually a JSON package containing everything needed for decryption).
Decrypting Your File:
- Choose the Encrypted File: This time, use the "Decrypt File" section. Click "Choose file to decrypt" and find the
.encor.jsonfile you created earlier. Drag and drop works for this step too. - Enter the Password: The password box will appear. Type in the exact password you used when you originally encrypted that file.
- Access Your Original File: With the correct password, the tool decrypts the data. Depending on the filetype, a preview may show directly in the browser (i.e., an image, some videos, PDFs, or text files). Then, you can download the original, decrypted file. The tool also shows some file details, including a hash check to help confirm the file hasn't been corrupted.
That's the core of it. The aim is to be straightforward while still using strong methods underneath.
Exploring the Advanced Options
I’ve included a few extra features that you might find particularly useful:
Password Management Features:
- Generate Random Password: If you're setting up encryption and want a strong, unique password, there’s a button in the password dialog: "Generate Random Password." It creates a 16-character password for you.
- Automatic Copy & Reminder: When a password is generated, the tool tries to copy it to your clipboard. A brief warning also shows up – this is important – stating that if this password is lost, the file can't be recovered. So, it's crucial to save it securely. There's also a manual "Copy Password" button.
- Password Strength Indicator: As you type a password (or when one is generated), a visual bar and a text label will give you an idea of its strength (Weak, Medium, Strong, or Very Strong).
Metadata Scrubbing & Size Obfuscation:
- When encrypting, you'll see a checkbox option: "Scrub metadata (JPEG EXIF, filename, type) & obfuscate size."
- For JPEG images, this can remove EXIF data (things like camera settings or sometimes embedded location info). It works by re-rendering the image.
- If you check this option for any file, it will also anonymize the original filename and file type information stored within the encrypted package. Additionally, it adds some random padding (between 50KB and 500KB) to the encrypted file's total size. This makes it harder to guess the original file's actual size or specific nature just from the encrypted file.
- (A quick note: Using the metadata scrubbing and padding feature changes the file's data. Because of this, the SHA-256 hash of your original file won't match the hash of the decrypted file. This is an expected outcome when using this feature, and the tool will mention this during decryption.)
Handling Multiple Files:
- If you select several files to encrypt at once, Local Encryption first bundles them into a single ZIP archive. Then, this one ZIP file is encrypted. When you decrypt, you'll get that ZIP file back, and you can then extract your original files from it.
How Your Security is Achieved (A Look at the Technology)
I think it's good to know what's going on behind the scenes to protect your files. Here are the main components:
The encryption algorithm.
At its core, the encryption uses AES (Advanced Encryption Standard), a method recognized across the globe for strong information defense. Your files get the protection of 256-bit keys, a length that provides an excellent security barrier. Working alongside AES is GCM, which stands for Galois/Counter Mode. What GCM brings to the table is crucial: it ensures more than just privacy for your data (confidentiality). It also provides robust checks to make sure the data is authentic and that it has maintained its integrity, meaning it confirms your file is exactly as you left it, without any modifications.
The Key Derivation Process (PBKDF2):
The password you enter (during the file encryption process) is not used directly as the encryption key. Instead, it is put through a function called PBKDF2 (Password-Based Key Derivation Function 2). Your password is mixed with a unique, randomly generated salt. A salt is just a bit of random data that ensures even if different people use the same password, their actual encryption keys will be unique. This password-and-salt mix is then processed 100,000 times using the SHA-256 algorithm. Running it through so many iterations makes it very computationally expensive for anyone trying to guess the password by trying many combinations (a brute-force attack).
The final output of all this is the strong 256-bit key that AES-GCM uses.
The Role of Salt and IV (Initialization Vector):
Beyond the unique salt used for your password, there's another layer of randomness. For each file you encrypt, the tool generates a completely new, random IV (that's an Initialization Vector) which AES-GCM uses in the process. Now, the combined effect of using a distinct salt for deriving the key and then a distinct IV for each encryption is really important. It means if you take the exact same file and encrypt it multiple times with the same password, every single encrypted version will be unique – they'll all look completely different from each other. This is a critical feature for strong security.
Web Workers for Performance:
Some operations, such as encrypting, decrypting, and particularly zipping multiple or large files, can be computationally demanding. So that these tasks don't interrupt your experience or make the browser page lag, the tool uses a Web Worker. This effectively lets those demanding processes run separately, ensuring the main page stays responsive.
Offline Capability
One of the nice things about this tool is that because it runs entirely in your browser, you don't need to be online to use it once the page itself has loaded. It also uses a Service Worker, which allows your browser to save the application files. This means it should load faster on subsequent visits and work more reliably even if your internet connection isn't perfect, giving it some PWA (Progressive Web App) characteristics.
Who Might Find Local Encryption Useful?
I imagine this tool being helpful for:
- Anyone who wants to ensure certain personal files remain private.
- People who need to store sensitive documents and want an added layer of security, even on their own computer or cloud storage (by encrypting them before uploading).
- Those who sometimes need to share confidential information and want to protect the files before sending them (the password would then be shared through a different, secure method).
- Users who appreciate tools that work transparently, without sending data to external servers.
A Note on Privacy
I want to emphasize this: Local Encryption is built so your files and passwords do not leave your computer during the encryption or decryption. They are not sent over the internet by this tool, nor are they stored on any server.
So, with that..
I put this tool together because I felt there was a need for a straightforward, reliable way to encrypt files locally. I hope it’s something that you can find a good use for.
